Sublime text the most liked text editor for web designer and developers. You might have seen pro developers using sublime text with beautiful layout and theme design. Today we will guide you through installing and configure some essential packages to customize sublime text and make it attractive and amazing.
Pre-requirement For Customization
Mainly, there are two ways to install packages for sublime text. One through package installer and the second is to install manually. In this tutorial, we will use package installer. If you are brand new to package installer, here is how you use it.
Package Installer is simple a way to add plugin or new feature to sublime text. By default, you can not use it in sublime text. You have to install it. It’s pretty simple. Just to go package controller site and install
package controller.
Depending on your sublime text version, copy the code they give you and open sublime text. Go to view > show console, past the code and press enter. It will install package controller. You will see two new options under the preferences. Package settings andPackage controller.
We will use package control for installing new packages. Click on the option and you will see a pop-op window. Type install package and enter. Wait until the new window open. Now you can install any package or theme you want.
Customize Sublime Text, Installing theme
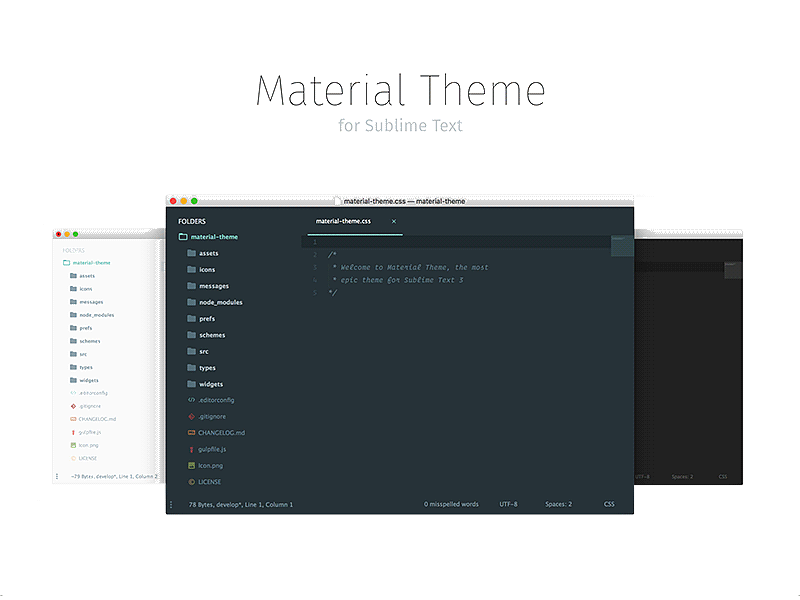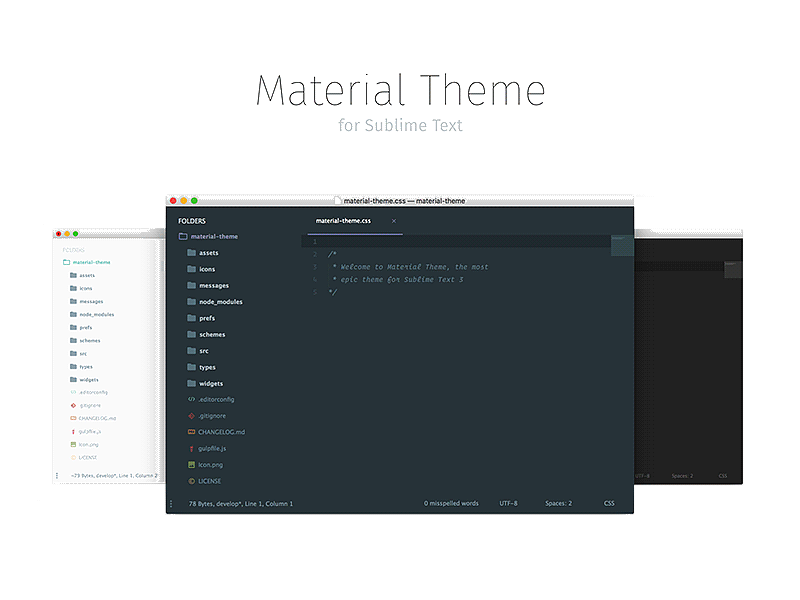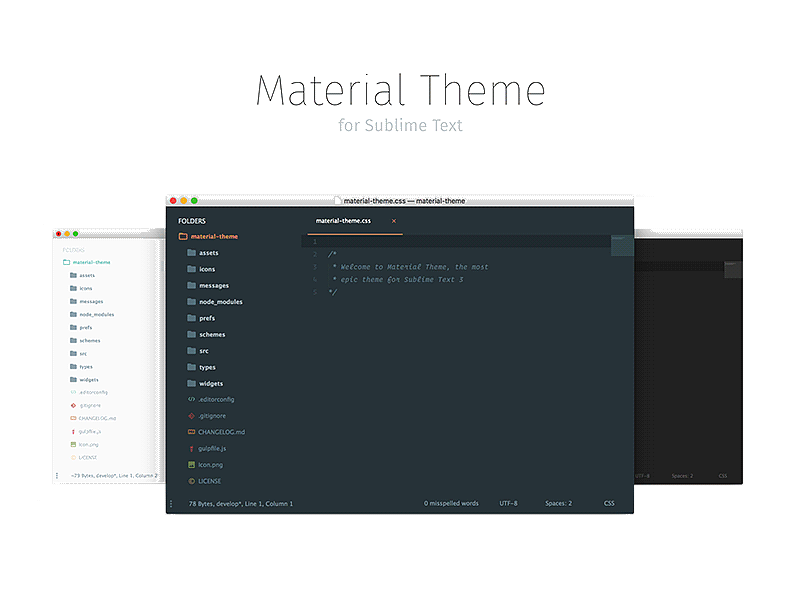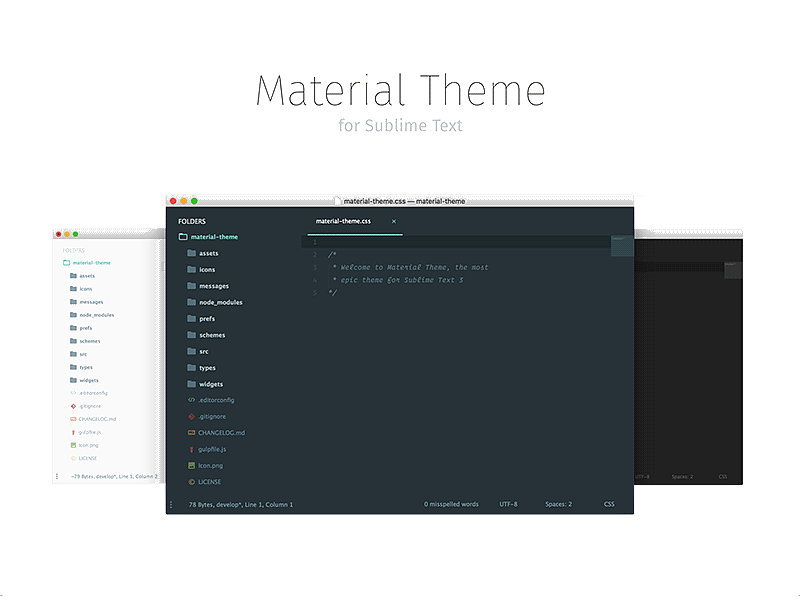
customize sublime text material theme
Material design and material theme is one of the most liked theme for sublime text and other text editors. You might have seen other pro developers who are using this them. Here is how you find it.
Where you install packages, search for Material theme and install. After installation, restart the Sublime text. Now you must can customize sublime text for current user.
Go to Preferences > settings – user.
You will see some default options. Customize it they way you want. Here is a basic customization options for material theme. Just copy and replace everything and save it.
|
|
{
"bold_folder_labels": false,
"color_scheme": "Packages/Colorsublime - Themes/Bittersweet.tmTheme",
"font_size": 14,
"ignored_packages":
[
"Vintage"
],
"theme": "Material Brogrammer.sublime-theme"
}
|
After saving the file, you will see the material theme effected.
For more options, check the documentation for material theme
here.
Install Color Sublime
Color Sublime is one of other great package for sublime text. It will help you customize sublime text color. Search for sublime colorsublime package and install.
To use color sublime, write colorsublime in package control instead of install package. And than you can install any theme color you want. If not sure search for Facebook, or bitterweet that looks good to me.
Conclusion
Now you know how to install package and themes. Feel free to search for other packages that you might like and install theme. I hope it has been informative for you. If you have any good package or question, feel free to share it on the comment bellow. 🙂